Zero Trust with Microsoft Endpoint Manager
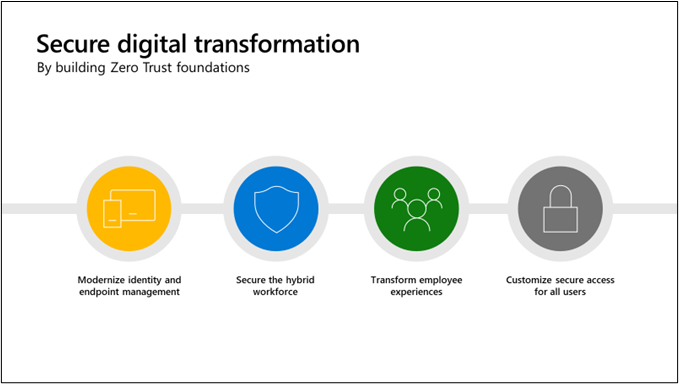
Zero Trust is a security strategy that evaluates all devices that are accessing your network, instead of blindly trusting them. This ensures that only healthy and compliant devices can access corporate resources, boosting data security.
Why does your company need a zero trust strategy? Because, over 90% of security incidents are caused by human error, and securing devices lowers your overall risk. In this article we will discuss how Microsoft Endpoint Manager can help you in achieving your zero risk goals.
A Better Alternative To The Honor Code
As a next-generation security solution, businesses are adopting Zero Trust to combat increased cyber threats. Rather than trusting all devices inside the corporate perimeter, zero trust requires validation at every step, making it more difficult for hackers to gain access and wreak havoc. Be sure that devices logging into your network are being used by trusted employees and are being maintained within company compliance.
Photo Credit: Microsoft Article “Build a strong Zero Trust Foundation starting with identity and endpoint management” by ByIrina Nechaeva, Jul 14 2021
An Easy Way To Get Started
One way to get started with Zero Trust is to implement multi-factor authentication. This will immediately strengthen your security by verifying user identities and reducing the risk of illegal access to corporate resources. Multi-factor authentication is easy to use and most people are already familiar with it, making it a great place to start when implementing Zero Trust. With Microsoft Endpoint Manager, you can easily setup multi-factor verification on all your devices.
Device Assessment
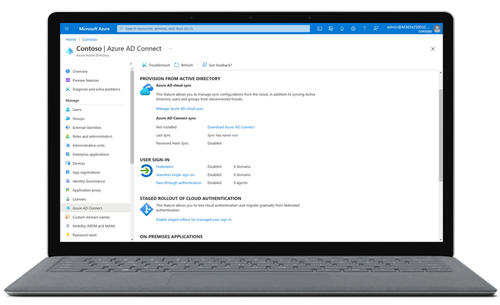
In order to allow devices access to company resources, a comprehensive assessment must be conducted to confirm each endpoint is trusted. In addition, security policies and malware risks should be taken into account to verify the health and compliance of the device. By registering the device with Azure AD, you can ensure a trusted identity. However, it is also crucial to establish protocols that differentiate between compliant and non-compliant devices before granting access.
Endpoint security
As part of a Zero Trust security strategy, it is important to secure employees' devices. This helps to maintain data security and business continuity. Employees' devices can be vulnerable due to running old operating systems or downloading unsafe apps. Microsoft Endpoint Manager can be used to instruct employees on safety protocols. In addition, Conditional Access policies can be used to control access by compliant and non-compliant devices. Another solution available is Microsoft Defender ATP, which allows you to identify attacks and block malware.
Photo Credit: Microsoft Article “Build a strong Zero Trust Foundation starting with identity and endpoint management” by ByIrina Nechaeva Published Jul 14 2021 08:00 AM
Restricting access
Azure AD Conditional Access policies should be configured specifically for your organization in order to ensure that only Intune-managed, domain-joined, and compliant devices have access to company resources. This approach allows for a more tailor-made response to the risks faced by your organization, while still preserving data security.
Policy enforcement
Although Intune Mobile Device Management (MDM) and Intune Mobile Application Management (MAM) provide a rigorous process for devices to gain access, security policies still need enforcement to control employee data access. Intune MAM will ensure that only compliant apps running on approved devices have specific access, preventing any potential breaches
Plugging the gaps
Businesses can benefit from improving their security posture by constantly upgrading their security solutions and assessing the health of their network. By identifying vulnerable points in the ecosystem, businesses can employ best practices for their security configuration and approach potential threats with stricter measures and constant monitoring of devices.
Photo Credit: Microsoft Article “Build a strong Zero Trust Foundation starting with identity and endpoint management” by ByIrina Nechaeva Published Jul 14 2021 08:00 AM
There are many considerations when developing and executing on a zero trust strategy for your organization. None of which should be taken lightly. Microsoft is a great resource when it comes to blogs, articles and videos. However, if you feel your company does not have the current bandwidth to accomplish your Zero Trust goals, then a Managed Services Provider is recommended.
You can easily find providers on LinkedIn and search engines. Though, if you would like to learn more about Managed Service Providers. right now, click the link below!
This Blog Post Was Co-Written By Ahsan Sattar & The C1st Tech Team